Spain
(21 %)
Spain
(21 %)
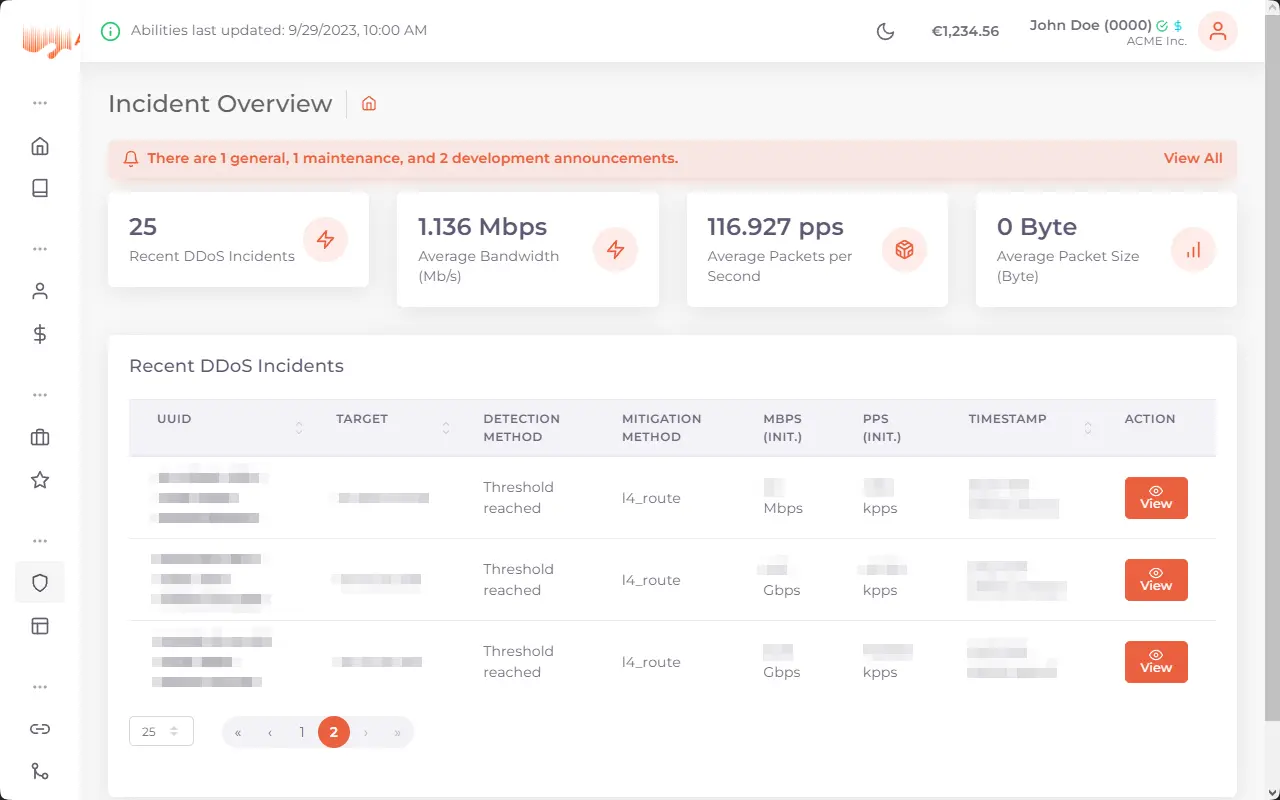
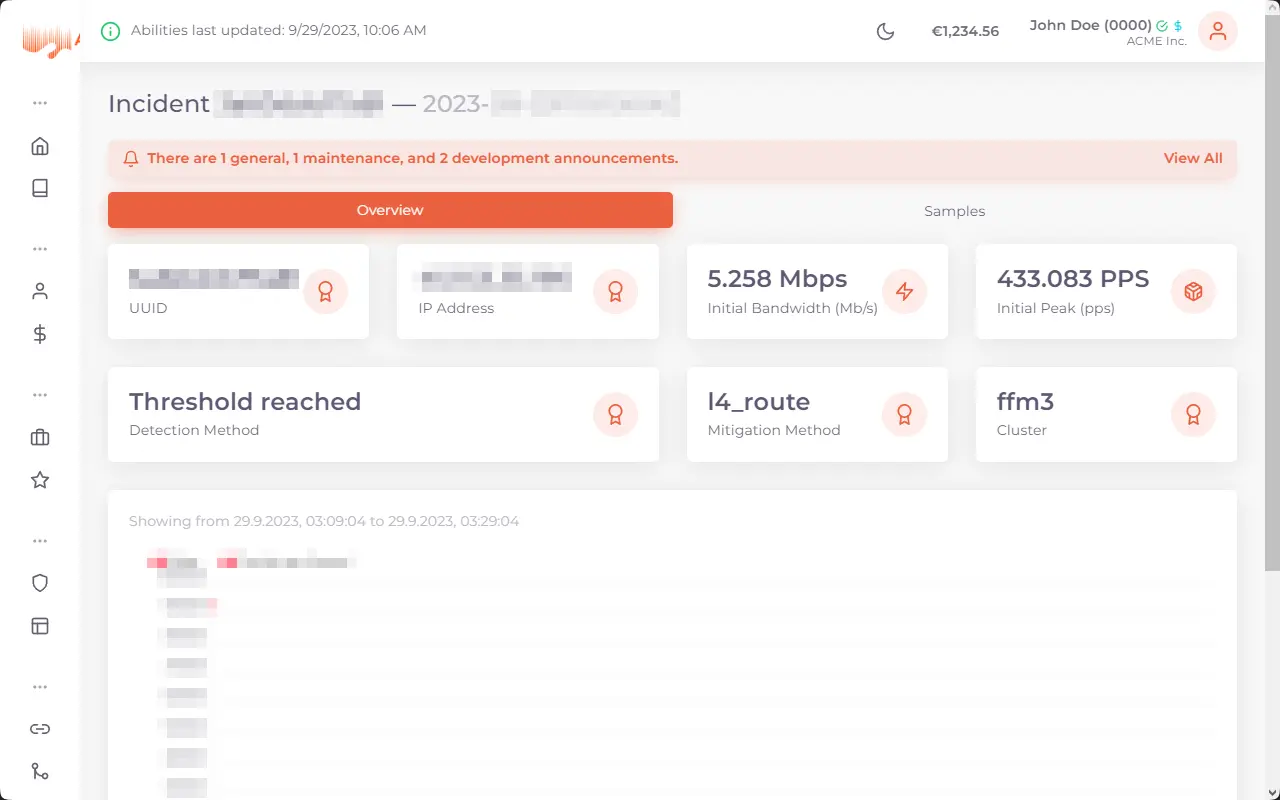
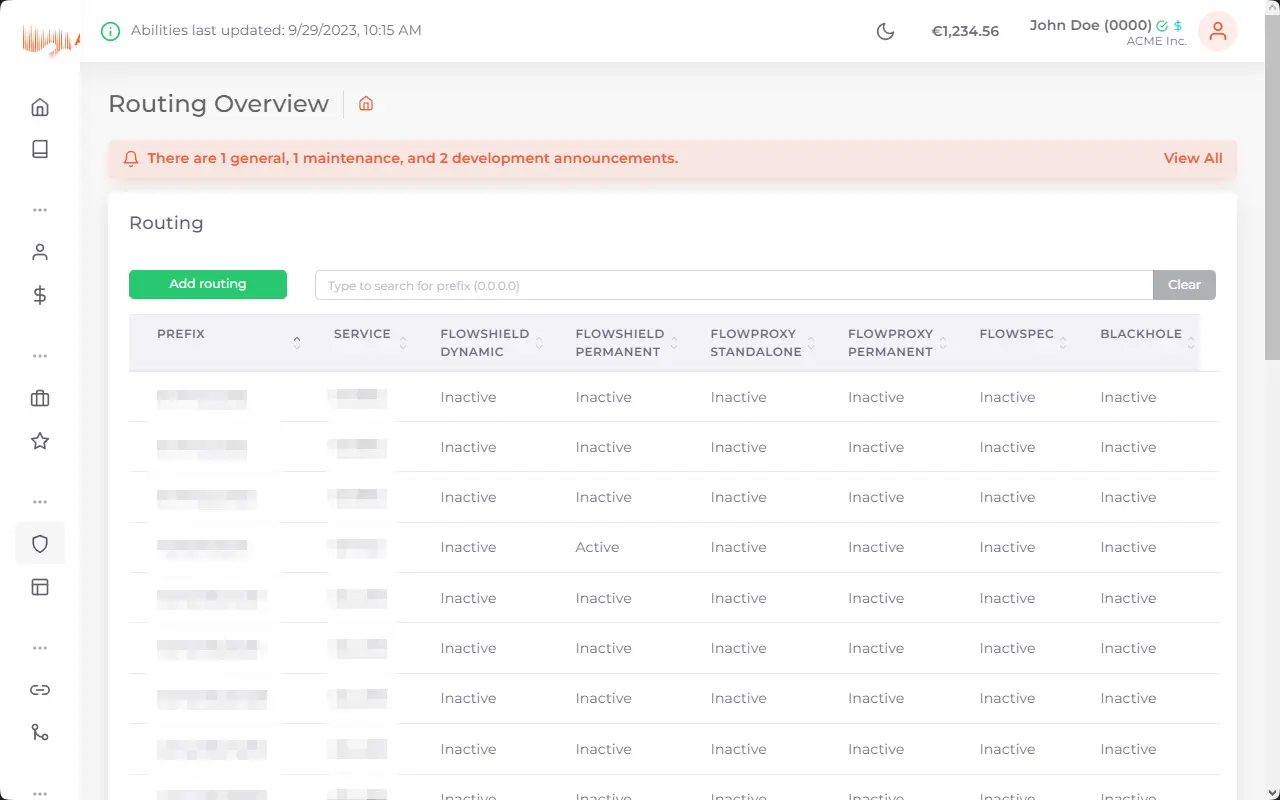
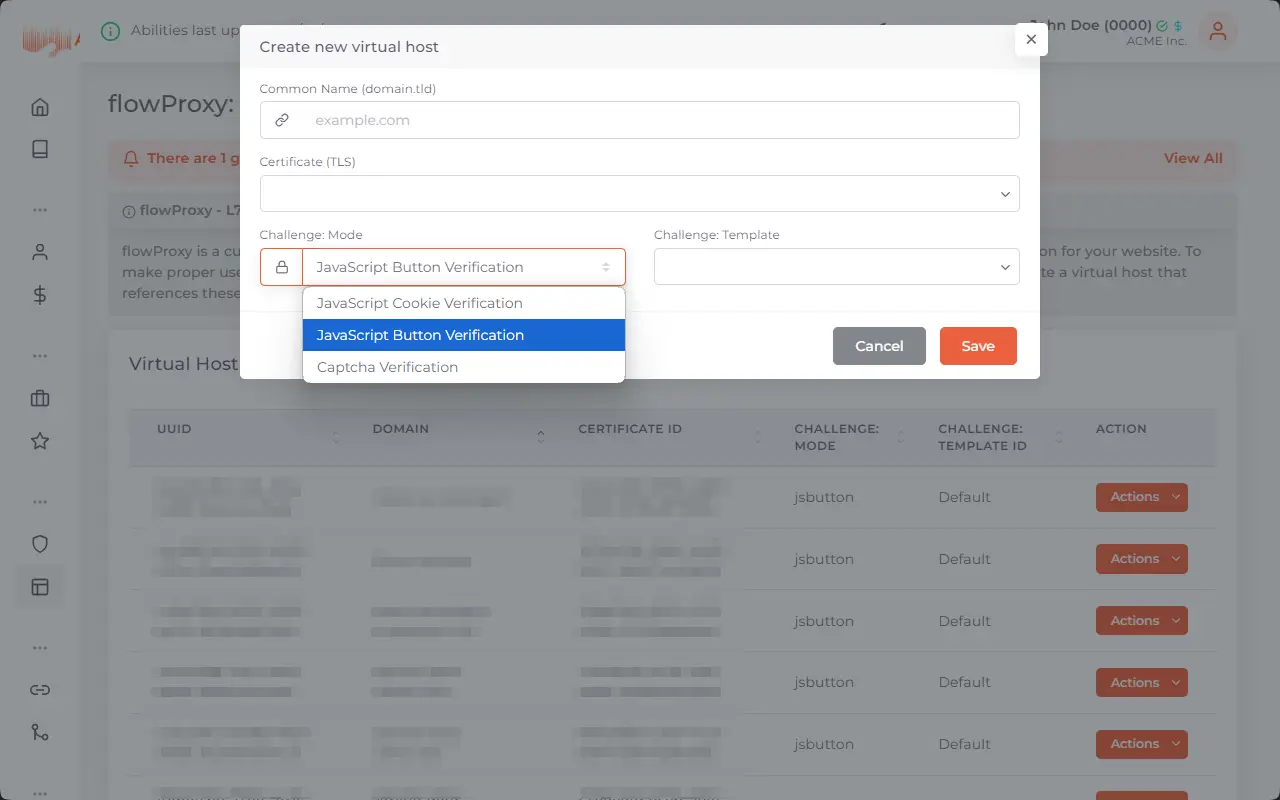
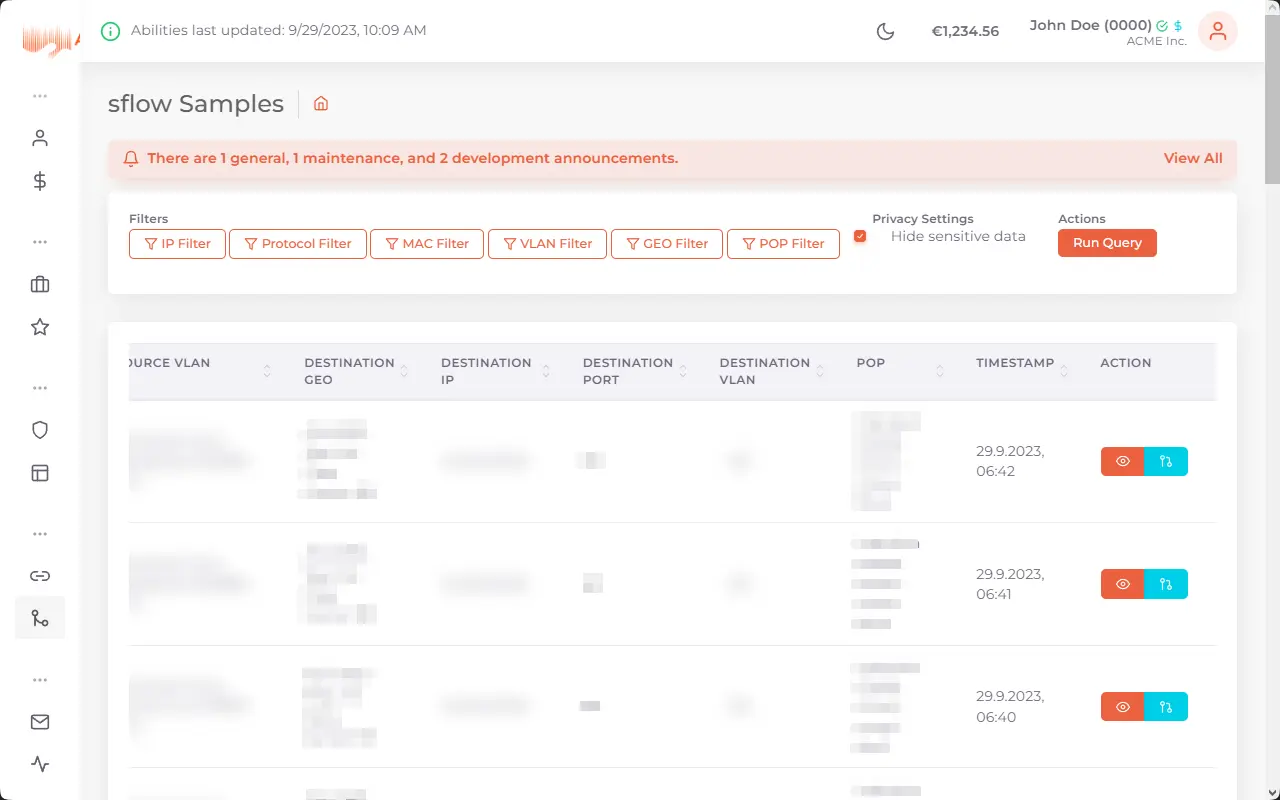
DDoS-Protection for your critical applications
Protect your online services from malicious attacks trying to render them offline. aurologic DDoS-Protection can be custom tailored and allows for high capacity.
Internet services these days are often targets of DDoS attacks, which flood the server with network requests so that it can not longer be reached to disrupt your operations and your reputation, which is the most important aspect of your business. aurologic DDoS-Protection protects your business from these attacks and is included free-of-charge with Cloud and Dedicated Servers as well as Colocation, while we offer the same to protect your externally hosted infrastructure with our in-house built software stack.
 Latvia
(21 %)
Latvia
(21 %)
 Ireland
(23 %)
Ireland
(23 %)
 Netherlands
(21 %)
Netherlands
(21 %)
 Austria
(20 %)
Austria
(20 %)
 Greece
(24 %)
Greece
(24 %)
 Croatia
(25 %)
Croatia
(25 %)
 Luxembourg
(17 %)
Luxembourg
(17 %)
 Cyprus
(19 %)
Cyprus
(19 %)
 Estonia
(20 %)
Estonia
(20 %)
 Malta
(18 %)
Malta
(18 %)
 Poland
(23 %)
Poland
(23 %)
 France
(20 %)
France
(20 %)
 Lithuania
(21 %)
Lithuania
(21 %)
 Portugal
(23 %)
Portugal
(23 %)
 Romania
(19 %)
Romania
(19 %)
 Sweden
(25 %)
Sweden
(25 %)
 Czech Republic
(21 %)
Czech Republic
(21 %)
 Germany
(19 %)
Germany
(19 %)
 Hungary
(27 %)
Hungary
(27 %)
 Slovenia
(22 %)
Slovenia
(22 %)
 Belgium
(21 %)
Belgium
(21 %)
 Finland
(24 %)
Finland
(24 %)
 Italy
(22 %)
Italy
(22 %)
 Bulgaria
(20 %)
Bulgaria
(20 %)
 Denmark
(25 %)
Denmark
(25 %)
 Slovakia
(20 %)
Slovakia
(20 %)